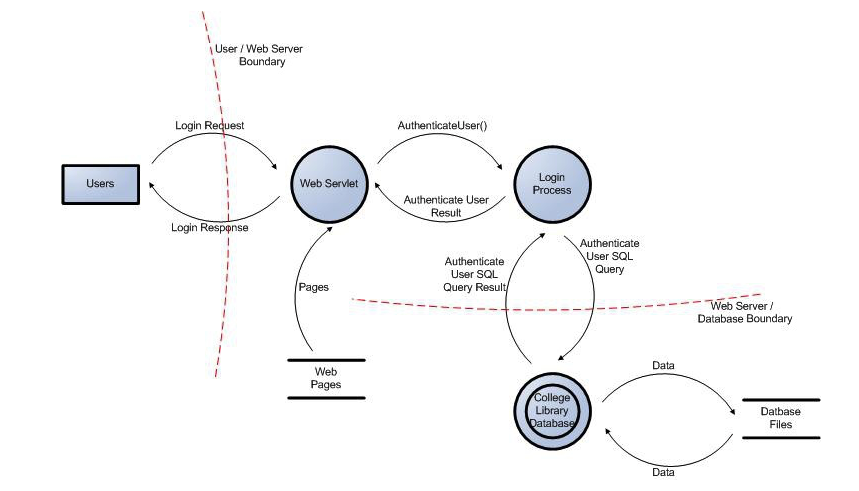
Initial AccessInitial access is the phase in which attackers first gain unauthorized entry into a target environment. This stage sets the foundation for further exploitation and persistence within the system. Attackers use a variety of methods to achieve initial access, including phishing, hardware placements, supply chain compromise, and exploiting public-facing applications.1. PhishingDefiniti..